
Get Dell EMC DES-9131 Exam Dumps
Dell EMC Specialist - Infrastructure Security, Version 1.0 Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

DES-9131 Desktop Practice
Test Software
Total Questions : 60

DES-9131 Questions & Answers
(PDF)
Total Questions : 60

DES-9131 Web Based Self Assessment Practice Test
Following are some DES-9131 Exam Questions for Review
In accordance with PR.MA, an organization has just truncated all log files that are more than 12 months old.
This has freed up 25 TB per logging server.
What must be updated once the truncation is verified?
A security audit of the systems on a network must be performed to determine their compliance with security policies. Which control should be used for the audit?
Which document is designed to limit damage, reduce recovery time, and reduce costs where possible to the organization?
Refer to the exhibit.
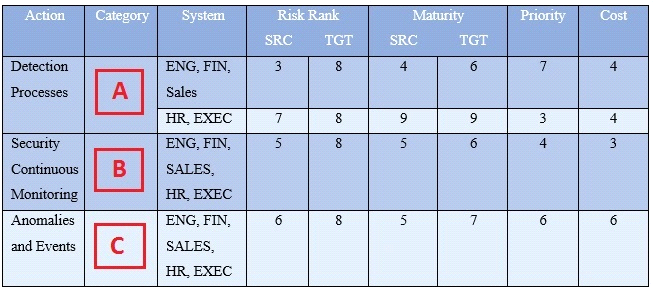
Your organization's security team has been working with various business units to understand their business requirements, risk tolerance, and resources used to create a Framework Profile.
Based on the Profile provided, what entries correspond to labels A, B, and C?

During what activity does an organization identify and prioritize technical, organizational, procedural,
administrative, and physical security weaknesses?
Unlock All Features of Dell EMC DES-9131 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support