
Get Dell EMC DEE-1421 Exam Dumps
Dell EMC Isilon Expert Solutions Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

DEE-1421 Desktop Practice
Test Software
Total Questions : 60

DEE-1421 Questions & Answers
(PDF)
Total Questions : 60

DEE-1421 Web Based Self Assessment Practice Test
Following are some DEE-1421 Exam Questions for Review
A company is planning to replicate a dataset to a newly implement Dell EMC Isilon cluster. SyncIQ will used from the source to the target cluster. The company's system administrator wants to know how long the initial synchronization will take seeding. The administrator provides the following information:
Link speed between clusters is 1 Gb/s
Link speed efficiency is 85%
SynclQ domain sue is 125 TB
If no SynctQ performance rules are set, what is the estimated number of days?
A Microsoft Windows administrator has an environment that includes a 4-node Dell EMC Isilon H500 cluster with one subnet and two pools. The administrator will use SMBv3 in all their clients. One pools for production using 10gigo-i and 10gige-2 ports from each node. The other pool is management using rngmt-1 from each node.
One of the concerns is the network throughput and how the administrator can get more than 10GbE throughput on the production pool on each node. Which recommendation should I provided''
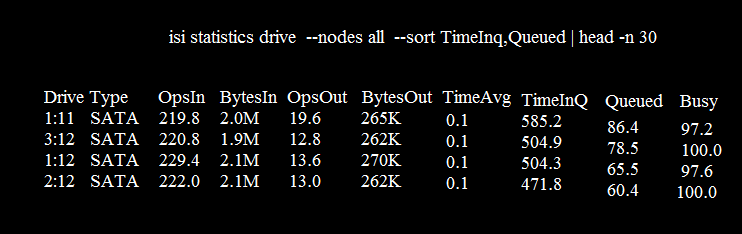
An administrator is investigating the performance of one of their Dell EMC Isilon clusters. Using the isi statistics drive command, the performance of the first five drives is shown.
Based on the exhibit, what represents the status of the drives?
A company has an environment with multiple AD in a one-way trust relationship. The AD provider on the cluster is configuring with SFU. The trusted domain is failing to supply UIDs and GIDs to the EMC Isilon cluster. As a result, user from the trusted domain is receiving an access denied error message.
What is a possible reason for the denial?
SynclQ policies are being configured between two Dell EMC Isilon clusters at a company's location. In addition, the company wants the ability to perform a failover at an Access zone level. Which actions should be performed to meet the requirements?
Unlock All Features of Dell EMC DEE-1421 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support