
Get Fortinet FCSS_SOC_AN-7.4 Exam Practice Questions - Real and Updated
Fortinet FCSS - Security Operations 7.4 Analyst Exam Dumps
Last Updated : Sep 3, 2025
Total Questions : 32
This Bundle Pack includes Following 3 Formats
Desktop Practice
Test software
Test software
Web Based
Practice Test
Practice Test
Questions &
Answers (PDF)
Answers (PDF)

FCSS_SOC_AN-7.4 Desktop Practice
Test Software
Last Updated : Sep 3, 2025
Total Questions : 32
Total Questions : 32
$59.00

FCSS_SOC_AN-7.4 Questions & Answers
(PDF)
Last Updated : Sep 3, 2025
Total Questions : 32
Total Questions : 32
$59.00

FCSS_SOC_AN-7.4 Web Based Self Assessment Practice Test
Last Updated : Sep 3, 2025
32 Total Questions
Supported Browsers
Supported Platforms
License Options
$59.00
Following are some FCSS_SOC_AN-7.4 Exam Questions for Review
Refer to the exhibit.
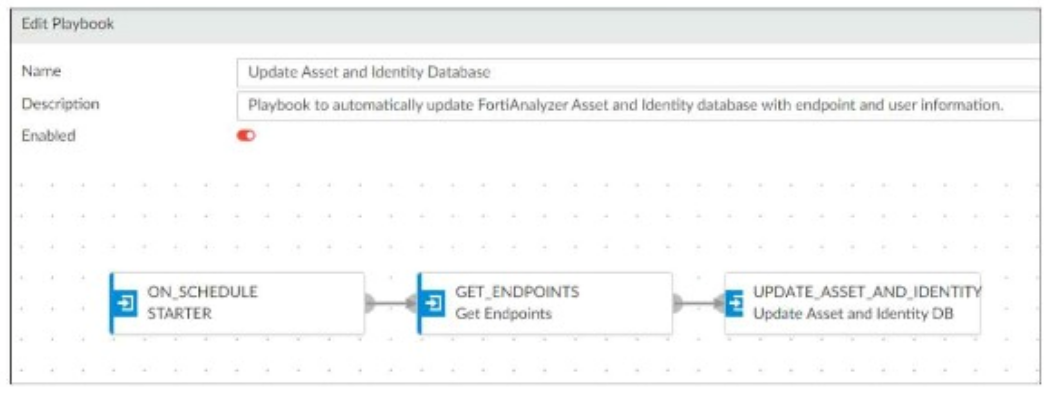
Which two options describe how the Update Asset and Identity Database playbook is configured? (Choose two.)
Refer to the exhibits.
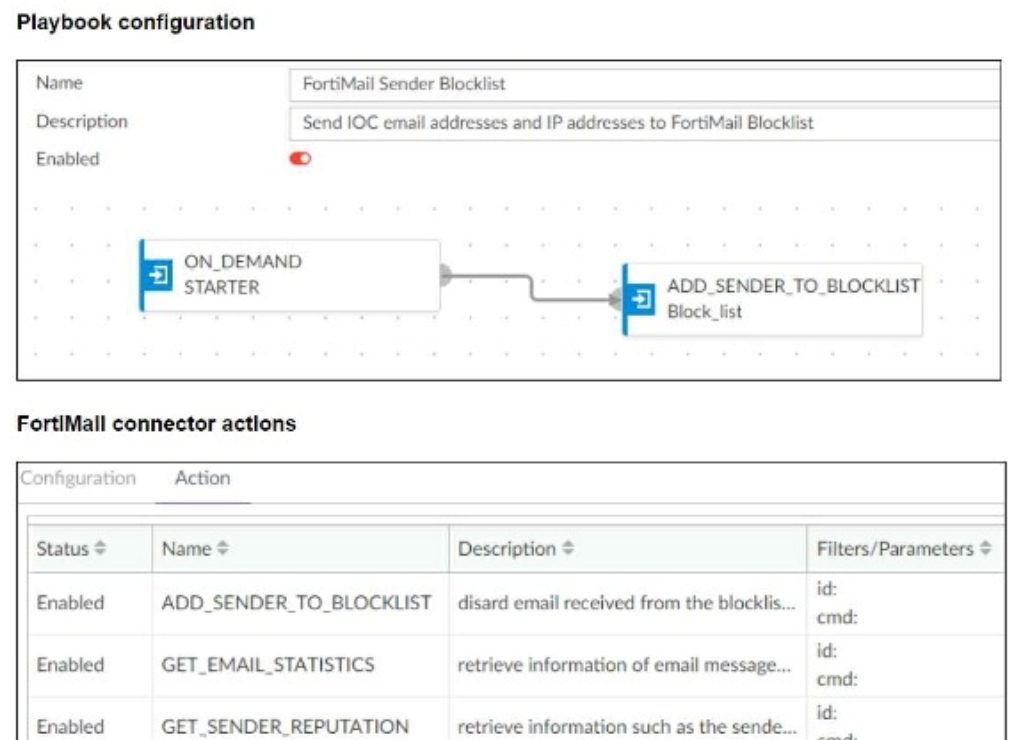
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
Refer to the exhibits.
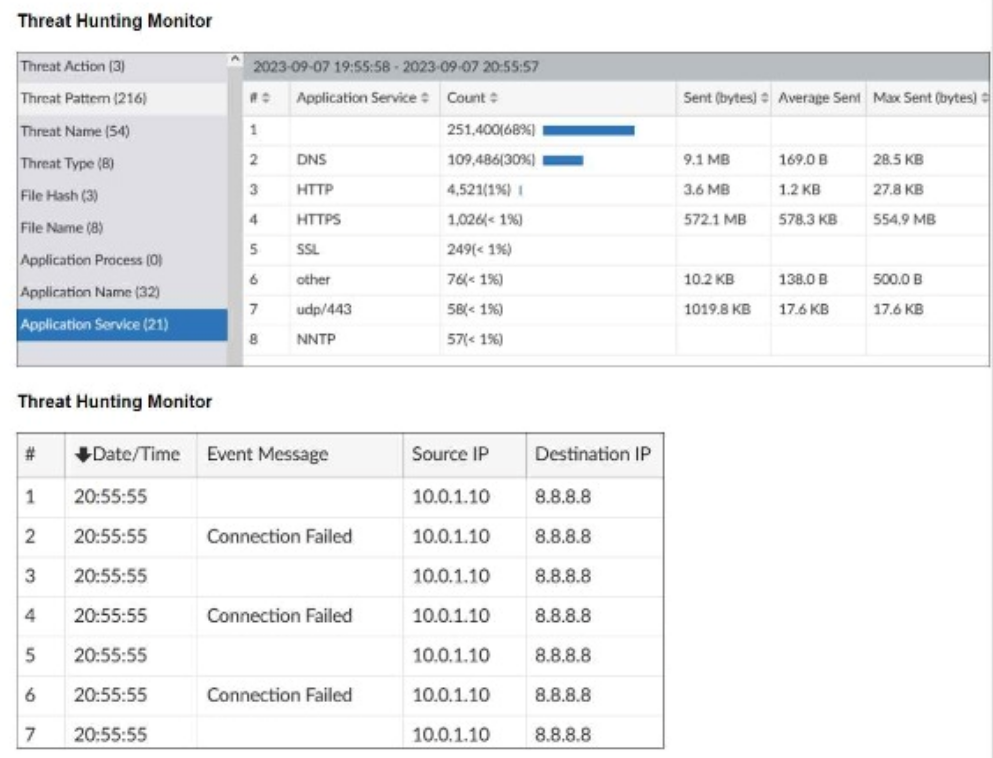
What can you conclude from analyzing the data using the threat hunting module?
Which role does a threat hunter play within a SOC?
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three.)
Unlock All Features of Fortinet FCSS_SOC_AN-7.4 Dumps Software
Just have a look at the best and updated features of our FCSS_SOC_AN-7.4 dumps which are described in detail in the following tabs. We are very confident that you will get the best deal on this platform.
Select Question
Types you want
Types you want
Set your desired
pass percentage
pass percentage
Allocate Time
(Hours: Minutes)
(Hours: Minutes)
Create Multiple
Practice test with
limited questions
Practice test with
limited questions
Customer
Support
Support
Latest Success Metrics For actual FCSS_SOC_AN-7.4 Exam
This is the best time to verify your skills and accelerate your career. Check out last week's results, more than 90% of students passed their exam with good scores. You may be the Next successful Candidate.
95%
Average Passing Scores in final Exam
91%
Exactly Same Questions from these dumps
90%
Customers Passed Fortinet FCSS_SOC_AN-7.4 exam













