
Get Fortinet FCSS_CDS_AR-7.6 Exam Practice Questions - Real and Updated
Fortinet FCSS - Public Cloud Security 7.6 Architect Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

FCSS_CDS_AR-7.6 Desktop Practice
Test Software
Total Questions : 38

FCSS_CDS_AR-7.6 Questions & Answers
(PDF)
Total Questions : 38

FCSS_CDS_AR-7.6 Web Based Self Assessment Practice Test
Following are some FCSS_CDS_AR-7.6 Exam Questions for Review
The cloud administration team is reviewing an AWS deployment that was done using CloudFormation.
The deployment includes six FortiGate instances that required custom configuration changes after being deployed. The team notices that unwanted traffic is reaching some of the FortiGate instances because the template is missing a security group.
To resolve this issue, the team decides to update the JSON template with the missing security group and then apply the updated template directly, without using a change set.
What is the result of following this approach?
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
Refer to the exhibit.
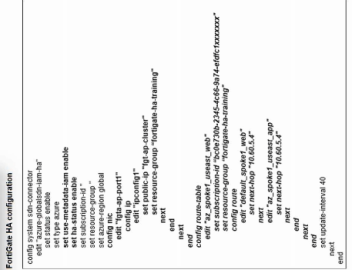
Refer to the exhibit.
You deployed a FortiGate HA active-passive cluster in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)
An AWS administrator must ensure that each member of the cloud deployment team has the correct permissions to deploy and manage resources using CloudFormation. The administrator is researching which tasks must be executed with CloudFormation and therefore require CloudFormation permissions.
Which task is run using CloudFormation?
Refer to the exhibit.
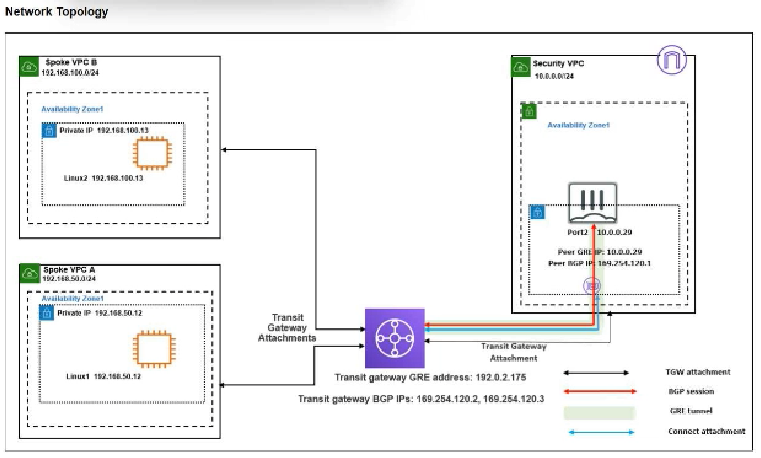
Refer to the exhibit.
You attempted to access the Linux1 EC2 instance directly from the internet using its public IP address in AWS. However, your connection is not successful.
Given the network topology, what can be the issue?
Unlock All Features of Fortinet FCSS_CDS_AR-7.6 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support













