
Get Fortinet FCP_FAZ_AN-7.4 Exam Practice Questions - Real and Updated
Fortinet FCP - FortiAnalyzer 7.4 Analyst Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

FCP_FAZ_AN-7.4 Desktop Practice
Test Software
Total Questions : 56

FCP_FAZ_AN-7.4 Questions & Answers
(PDF)
Total Questions : 56

FCP_FAZ_AN-7.4 Web Based Self Assessment Practice Test
Following are some FCP_FAZ_AN-7.4 Exam Questions for Review
You must find a specific security event log in the FortiAnalyzer logs displayed in FortiView, but, so far, you have been uncuccessful.
Which two tasks should you perform to investigate why you are having this issue? (Choose two.)
You are tasked with finding logs corresponding to a suspected attack on your network.
You need to use an interface where all identified threats within timeframe are listed and organized. You also need to be able to quickly export the information to a PDF file.
Where can you go to accomplish this task?
A playbook contains five tasks in total. An administrator runs the playbook and four out of five tasks finish successfully, but one task fails.
What will be the status of the playbook after it is run?
Refer to Exhibit:
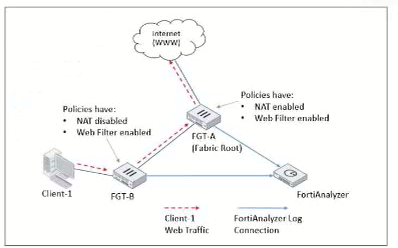
Client-1 is trying to access the internet for web browsing.
All FortiGate devices in the topology are part of a Security Fabric with logging to FortiAnalyzer configured. All firewall policies have logging enabled. All web filter profiles are configured to log only violations.
Which statement about the logging behavior for this specific traffic flow is true?
Which two actions should an administrator take to vide Compromised Hosts on FortiAnalyzer? (Choose two.)
Unlock All Features of Fortinet FCP_FAZ_AN-7.4 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support













