
Get Fortinet FCP_FAC_AD-6.5 Exam Practice Questions - Real and Updated
Fortinet FCP - FortiAuthenticator 6.5 Administrator Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

FCP_FAC_AD-6.5 Desktop Practice
Test Software
Total Questions : 30

FCP_FAC_AD-6.5 Questions & Answers
(PDF)
Total Questions : 30

FCP_FAC_AD-6.5 Web Based Self Assessment Practice Test
Following are some FCP_FAC_AD-6.5 Exam Questions for Review
Which two behaviors do certificate revocation lists (CRLs) on FortiAuthenticator exhibit? (Choose two.)
At a minimum, which two configurations are required to enable captive portal services on FortiAuthenticator? (Choose two.)
An administrator has just learned that an intermediate CA certificate signed by a FortiAuthenticator device acting as the Root CA has been compromised.
Which two steps should the administrator take to resolve the security issue? (Choose two.)
Refer to the exhibit.
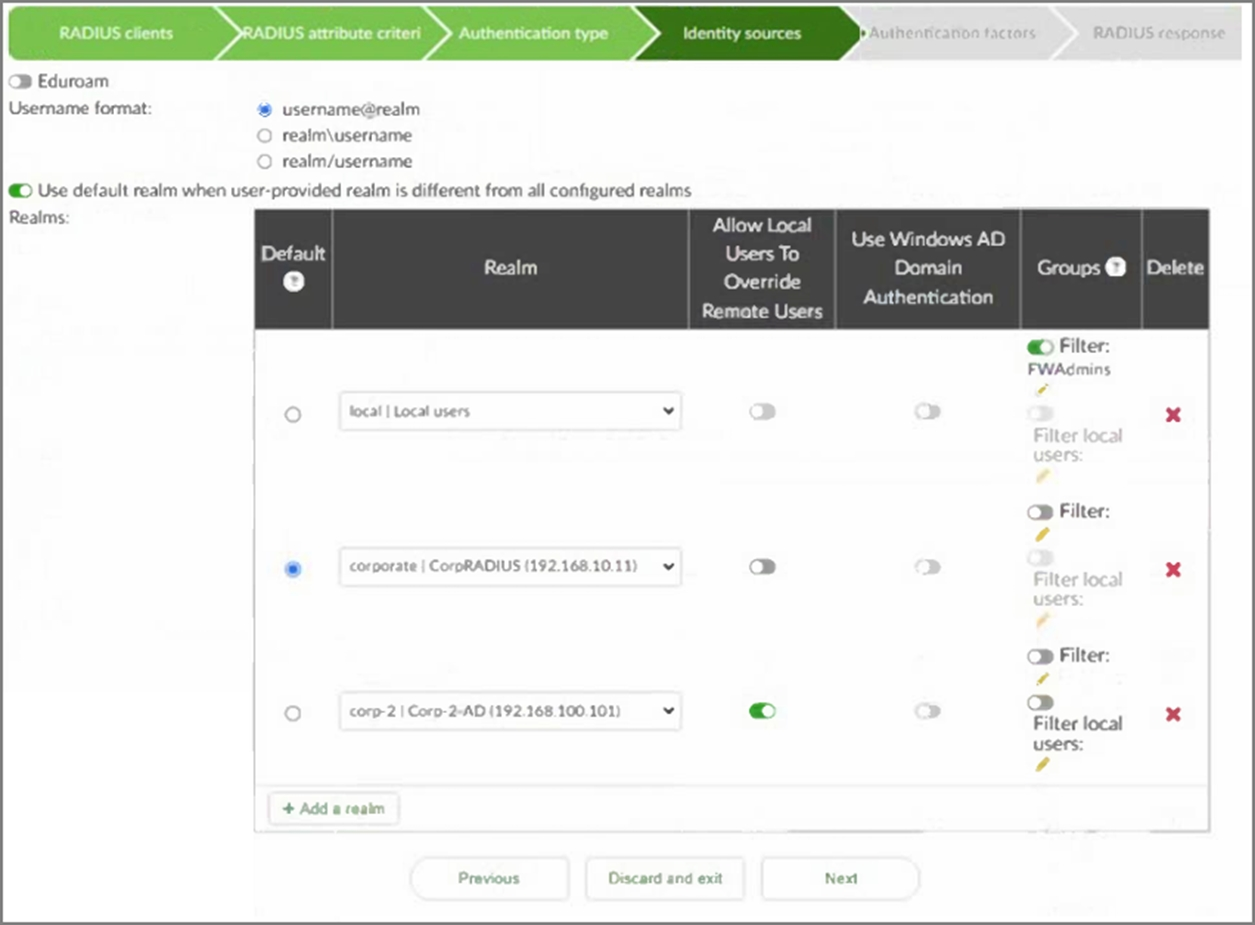
Examine the RADIUS policy configuration shown in the exhibit. A user attempts to authenticate by entering the username jdoe@example.com and their password.
Which realm will the user be authenticated against?
You have implemented two-factor authentication to enhance security to sensitive enterprise systems.
How could you bypass the need for two-factor authentication for users accessing form specific secured networks?
Unlock All Features of Fortinet FCP_FAC_AD-6.5 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support












