
Get HashiCorp Vault-Associate Exam Practice Questions - Real and Updated
HashiCorp Certified: Vault Associate (002) Exam Dumps
Last Updated : Sep 3, 2025
Total Questions : 57
This Bundle Pack includes Following 3 Formats
Desktop Practice
Test software
Test software
Web Based
Practice Test
Practice Test
Questions &
Answers (PDF)
Answers (PDF)

Vault-Associate Desktop Practice
Test Software
Last Updated : Sep 3, 2025
Total Questions : 57
Total Questions : 57
$59.00

Vault-Associate Questions & Answers
(PDF)
Last Updated : Sep 3, 2025
Total Questions : 57
Total Questions : 57
$59.00

Vault-Associate Web Based Self Assessment Practice Test
Last Updated : Sep 3, 2025
57 Total Questions
Supported Browsers
Supported Platforms
License Options
$59.00
Following are some Vault-Associate Exam Questions for Review
How would you describe the value of using the Vault transit secrets engine?
The vault lease renew command increments the lease time from:
You can build a high availability Vault cluster with any storage backend.
Which of the following is a machine-oriented Vault authentication backend?
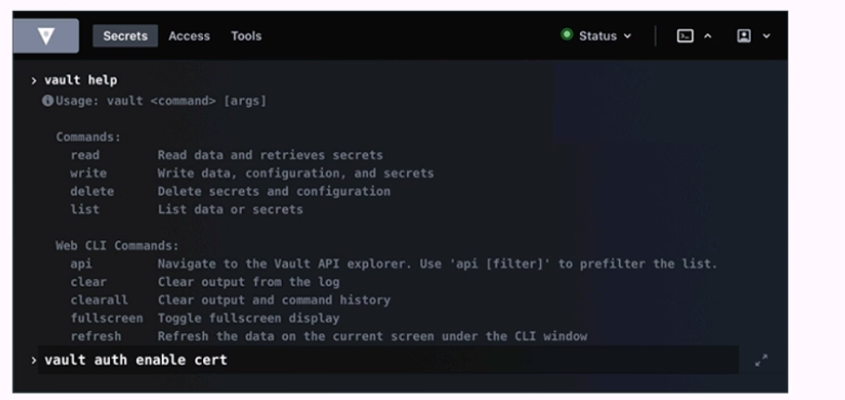
Running the second command in the GUI CLI will succeed.
Unlock All Features of HashiCorp Vault-Associate Dumps Software
Just have a look at the best and updated features of our Vault-Associate dumps which are described in detail in the following tabs. We are very confident that you will get the best deal on this platform.
Select Question
Types you want
Types you want
Set your desired
pass percentage
pass percentage
Allocate Time
(Hours: Minutes)
(Hours: Minutes)
Create Multiple
Practice test with
limited questions
Practice test with
limited questions
Customer
Support
Support
Latest Success Metrics For actual Vault-Associate Exam
This is the best time to verify your skills and accelerate your career. Check out last week's results, more than 90% of students passed their exam with good scores. You may be the Next successful Candidate.
95%
Average Passing Scores in final Exam
91%
Exactly Same Questions from these dumps
90%
Customers Passed HashiCorp Vault-Associate exam












