
Get Cisco 300-910 Exam Dumps
Cisco Implementing DevOps Solutions and Practices using Cisco Platforms Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

300-910 Desktop Practice
Test Software
Total Questions : 130

300-910 Questions & Answers
(PDF)
Total Questions : 130

300-910 Web Based Self Assessment Practice Test
Following are some 300-910 Exam Questions for Review
Refer to the exhibit.
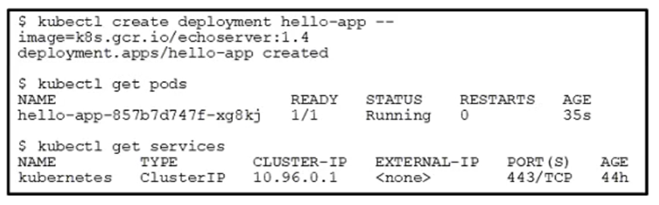
Which action allows the development team to reach the deployed application?
Which approach must be used to integrate DevOps practices into the team structure in an existing organization?
Refer to the exhibit.

The text represents a syslog message sent from a Linux server to a centralized log system.
Based on the format of the log message, how must the functionality of the log parser be extended to improve search capabilities?
Refer to the exhibit.
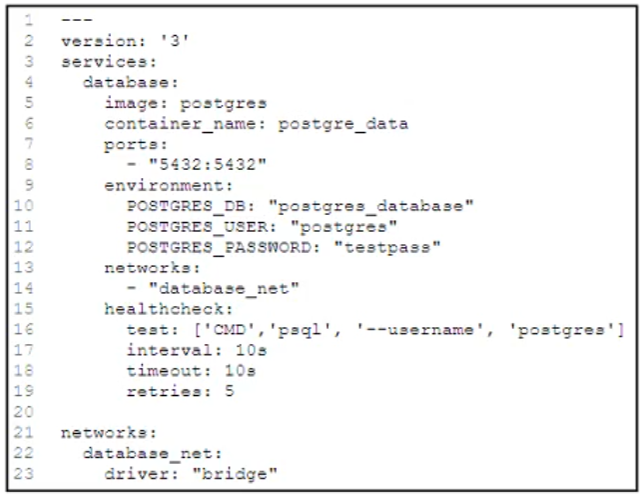
A docker-compose.yml file implements a postgres database container.
Which .gitlab-ci.yml code block checks the health status of the container and stops the pipeline if the container is unhealthy?
A)
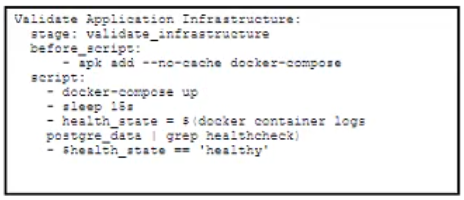
B)
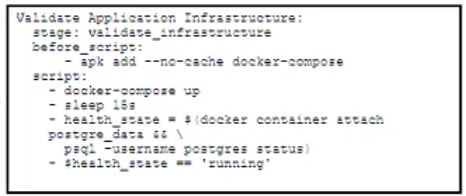
C)
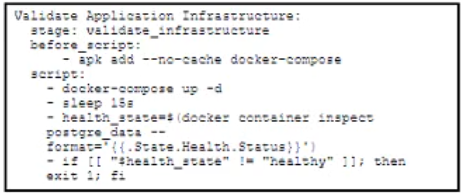
D)
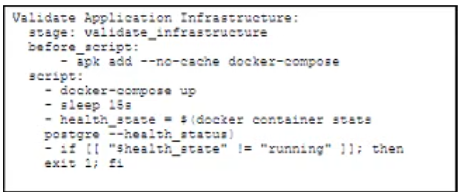
Refer to the exhibit.
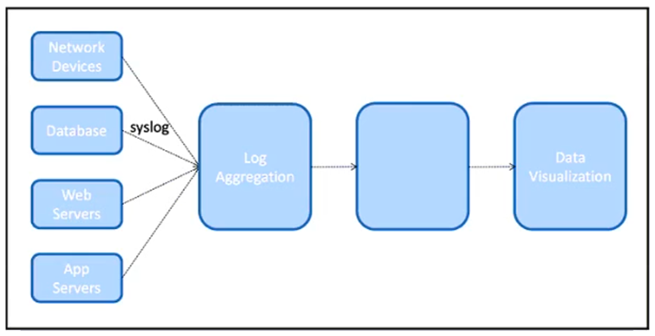
The IT team is creating a new design for a logging system. The system must be able to collect logs from different components of the infrastructure using the SNMP protocol. When the data is collected it will need to be presented in a graphical UI to the NOC team.
What is the architectural component that needs to be placed in the unlabeled box to complete this design?
Unlock All Features of Cisco 300-910 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support