
Get Cisco 200-201 Exam Dumps
Cisco Understanding Cisco Cybersecurity Operations Fundamentals Exam Dumps
This Bundle Pack includes Following 3 Formats
Test software
Practice Test
Answers (PDF)

200-201 Desktop Practice
Test Software
Total Questions : 311

200-201 Questions & Answers
(PDF)
Total Questions : 311

200-201 Web Based Self Assessment Practice Test
Following are some 200-201 Exam Questions for Review
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
Refer to the exhibit.
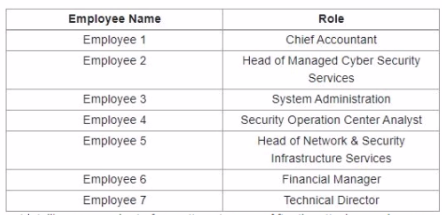
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
According to CVSS, what is a description of the attack vector score?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)
Unlock All Features of Cisco 200-201 Dumps Software
Types you want
pass percentage
(Hours: Minutes)
Practice test with
limited questions
Support